VeilNet
Connect Anything, Secure Everything
An intelligent, secure network for AI-powered world and beyond
Join the waitlist for early access of VeilNet Private Realm
Your exclusive, isolated overlay network with customizable IP address range, Geo-location restriction and full-stack access.
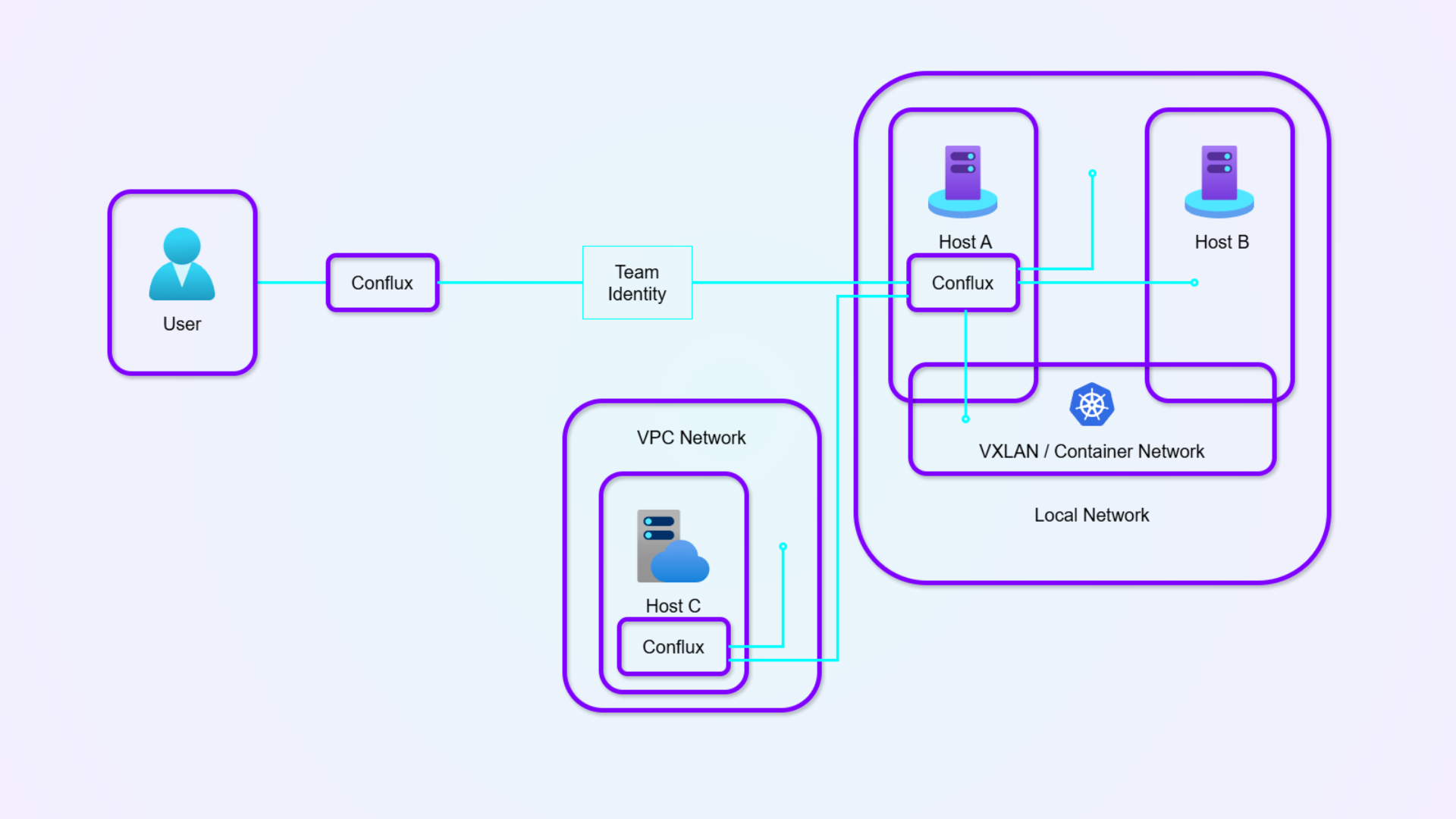
Replace your mesh overlay VPN
No more sub-routers, no mesh floods, no ACL explosion. VeilNet replaces the entire mesh overlay with one Conflux per location and a unified identity system. Full-stack access — host LANs, VXLANs, containers, VPCs — all secured and routed without manual configuration.
Deploy VeilNet in Three Steps
Just connect and code, make your infrastructure work for you.
Step 1: Obtain a registration token
Sign up at console.veilnet.app and generate a registration token. It's free and easy.
Step 2: Deploy VeilNet Conflux
Deploy VeilNet Conflux on your server, docker or kubernetes with one command / manifest. It takes less than 1 minute.
Step 3: Enjoy the unlimited connectivity
Install VeilNet Conflux on your device or use our GUI application to access your entire infrastructure with zero configuration.
Things that make VeilNet different
Beyond Zero-Trust
The one and only system that adopts both Kyber KEM and Dilithium DSA, two post-quantum cryptography standards approved by NIST.
VeilNet provides Packet Level Authentication (PLA) to prevent any unwanted access even if your local network is compromised.
Network breach becomes a distant memory.
Full-Stack Access
One VeilNet Conflux instance per location unlocks full-stack access: host LANs, VXLANs, containers, VPCs, and AI agents.
No metadata injection, no MTU loss, no routing table pollution, and no sub-routers, VeilNet remains fully compatible with your existing network while providing accessbility to your entire infrastructure, no matter local or remote.
AI Powered Network
The unique Reinforcement Learning algorithm in VeilNet allows the network to continuously optimize itself.
It creates independent secure streams for each destination, builds multi-hop paths to avoid congestion, and finds peer relays to improve throughput.
Your network is always optimized and always available.
