Your Network, Your Rules
VeilNet Private Realm grants you a hidden realm — a parallel network carved out of cyberspace and bound to your will.
Join the waitlist and become part of the pantheon defining the future of cyberspace.
One Command
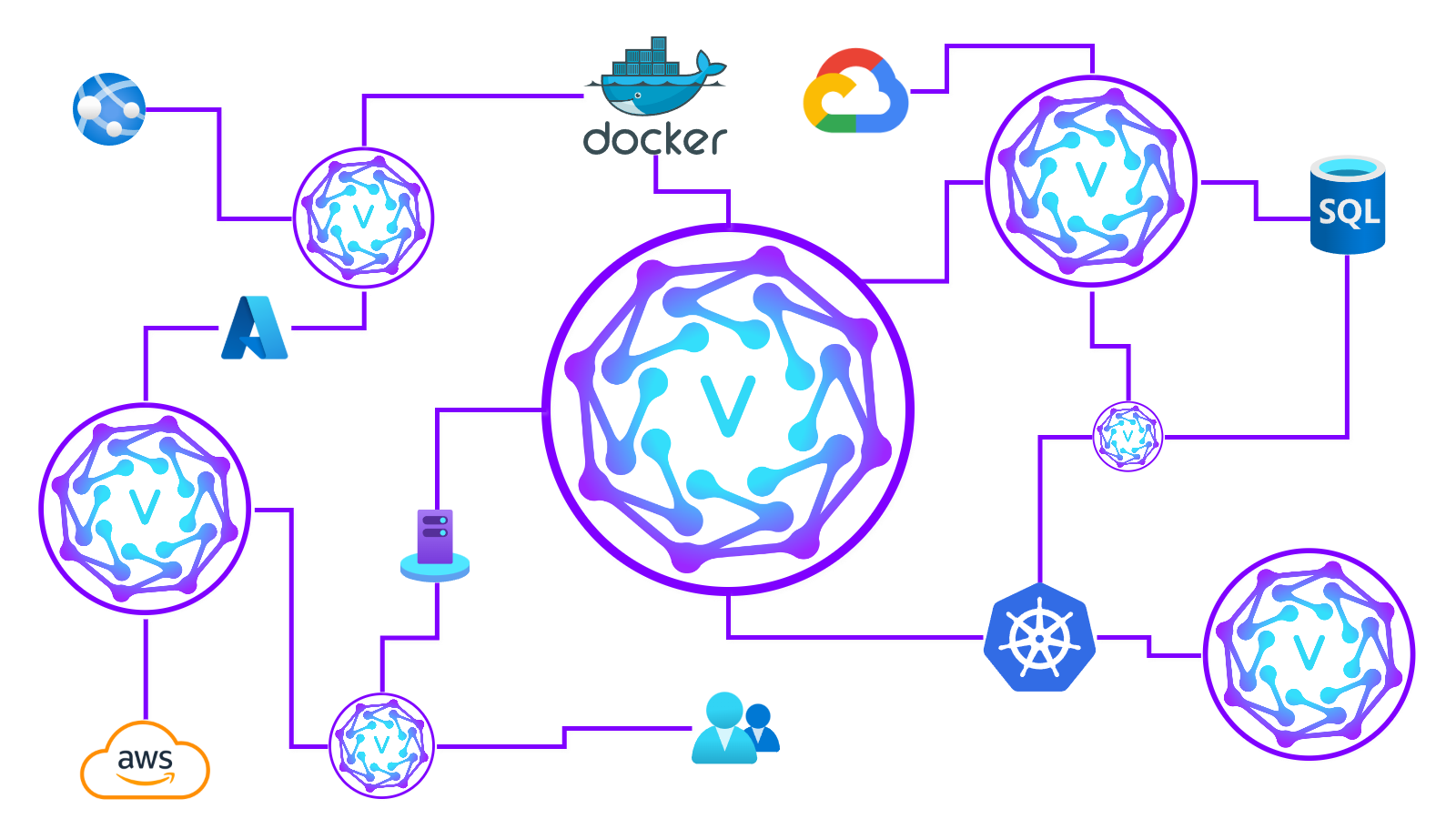
Deploy VeilNet with a single command — no configuration files, no routing rules, no network plumbing.
Our intelligent Reinforcement Learning engine automatically discovers,
maintains, and optimizes paths across your entire stack, whether it lives in VPCs, VXLANs,
containers, bare-metal, or remote edge nodes.
sudo ./veilnet-conflux register -p -t <registration_token>
One Deployment
VeilNet is one of the few modern systems not built on WireGuard, and therefore avoids all of its
structural limits. We do not inject metadata into IP packets, do not truncate or repad frames,
and do not pollute host routing tables with per-peer entries.
A single deployment per location gives you full-stack access to host LANs, container networks,
virtual overlays, and remote subnets — all without sub-routers or manual configuration.
docker run -d --name veilnet-conflux -e VEILNET_REGISTRATION_TOKEN=<registration_token> -e VEILNET_PORTAL=true --privileged veilnet/conflux:beta
One Subscription
VeilNet's decentralized overlay delivers true linear scalability. More devices and more users do not
multiply load on our infrastructure, because no global mesh or persistent tunnels exist.
We could enforce artificial device caps like other vendors, but we choose not to.
Instead, our architecture returns this efficiency back to you — one subscription, and everything scales.
Breaking the Boundaries of Networking
Each VeilNet capability represents a category-defining advancement beyond traditional networking.
Post-Quantum Cryptography
VeilNet is the one and only system that adopts post-quantum cryptography into both encryption and authentication. (Kyber KEM and Dilithium DSA)
Decentralized SDN
VeilNet is the one and only Software Defined Network without centralized controllers, but cooperative agents.
AI-Powered Network
VeilNet is the one and only network that directly integrates AI into its routing algorithm. (Reinforcement Learning)
Sub Millisecond Overhead
VeilNet is the one and only overlay that consistently achieves sub-millisecond overhead even with post-quantum cryptography.
Full-Stack Access
VeilNet is the one and only system that gives direct access to host LANs, container networks, overlays, VPCs, and remote subnets — without sub-routers or manual configuration.
No MTU Loss
VeilNet is the one and only VPN that never truncates, pads, or rewrites frames — and never injects metadata into IP packets.
Packet Level Authentication
VeilNet is the one and only production system that authenticates the sender identity of every single packet using post-quantum cryptography.
No Peer Synchronization
VeilNet is the one and only overlay network that requires zero peer lists, zero peer sync, and zero per-peer routing entries.
No Coordination Server
VeilNet is the one and only overlay network without a central rendezvous, NAT punch server, or broker — cooperative agents self-organize through a global control fabric.
Ephemeral Links
VeilNet is the one and only network that creates and dissolves links on-demand per-destination, eliminating idle attack surfaces and avoiding the complexity of always-on tunnels.
Independent Per-Destination Streams
VeilNet is the one and only overlay where each destination uses an independent encrypted stream — no shared tunnel, no shared congestion, no shared metadata.
True Multi-Hop & Multi-Path
VeilNet is the one and only production overlay with native multi-hop, multi-path forwarding without mesh dependency or manual relay configuration.
No Fixed Servers
VeilNet is the one and only VPN without fixed servers or static endpoints — the network forms itself dynamically and disappears when idle.
Invisible & Unobservable Traffic
VeilNet is the one and only overlay where no metadata, public keys, or protocol fingerprints appear on the wire — indistinguishable from random noise.
Self-Healing Overlay Fabric
VeilNet is the one and only overlay that automatically re-routes, repairs, and reconstructs paths across clouds, regions, and ISPs with zero restarts.
Use Cases
VeilNet is designed to solve real-world problems in a way that traditional networking cannot.
Multi-Region Super Cluster
Traditionally, a multi-region cloud deployment means running separate clusters in each region, stitched together with a fragile service mesh. Resources such as config maps, certificates, and secrets are duplicated — never truly shared.
This is because conventional overlay networks cannot scale with multi-region cloud systems, are incompatible with technologies like VXLAN, and rely on sub-routers that cannot adapt to modern elastic infrastructure.VeilNet redefines multi-region architecture by letting you create a single logical cluster that spans all regions. All resources — and all elasticity — are shared across the entire topology.
No more repetitive deployments. Rolling out features or updates across regions becomes a single operation that completes in minutes.
Virtual Air Gap
A physical air gap isolates a network from external access, but once an attacker gains an internal foothold, there is often no defense against lateral movement.VeilNet's Packet Level Authentication (PLA) enables a virtual air-gapped network where every packet is encrypted and authenticated using post-quantum identities.
Even if an attacker compromises a host, they still cannot access protected services — not even with a quantum computer — because they do not possess a valid packet-level identity.
Secure Development Environment
Modern development involves AI agents, multi-cloud systems, SaaS platforms, and hybrid infrastructure.
Creating a secure environment across all of these components has become a nightmare of peering, sub-routers, and fragile manual configuration.VeilNet's identity-affinity access control secures your environment based on who is using it, not which IP, subnet, or cloud provider they belong to.
Regardless of where services run, VeilNet enforces a unified, identity-driven security model — simple, predictable, and cloud-native.
Edge Computing / AI Workers
Edge compute and AI workers demand massive horizontal scale. Traditional overlay VPNs cannot keep up, often collapsing into one connector with layers of sub-routers for every subnet agents live in.
This creates bottlenecks for bandwidth, elasticity, and overall system performance.VeilNet Conflux scales horizontally without sub-routers. Each AI agent or edge worker can run its own Conflux instance without exploding into millions of static tunnels.
Thanks to VeilNet's decentralized, multi-hop design, the network becomes more resilient, efficient, and self-optimising as more workers join the system.
