In most industries, the divide between IT and OT remains as wide as ever. While IT systems have evolved toward cloud-native, API-driven architectures, OT environments are still dominated by legacy controllers and serial protocols designed long before cybersecurity was a concern. To protect these fragile systems, organisations have relied on strict network segregation — the so-called “air gap.” Yet this isolation is less a mark of good security than a symptom of technological stagnation: OT devices often lack encryption, authentication, or even basic access control. In a world moving toward autonomous decision-making and AI-driven optimisation, these outdated foundations make safe connectivity nearly impossible.
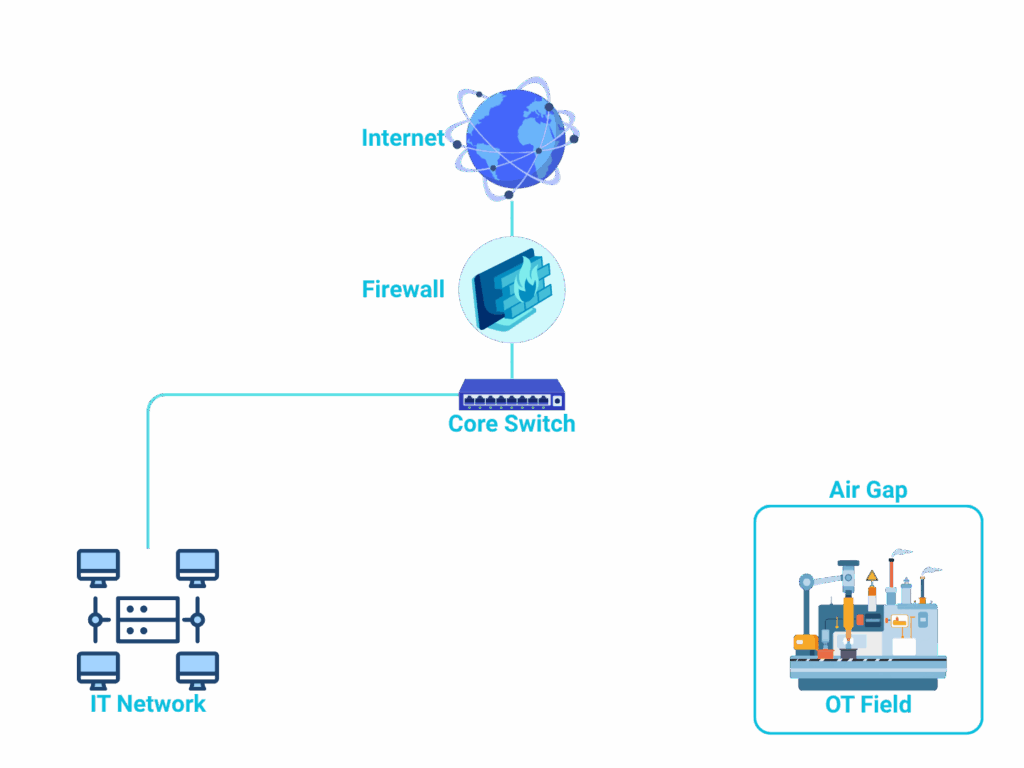
The rise of Industry 4.0 brought a new wave of connectivity — intelligent sensors, cloud analytics, and AI-driven automation. But this digital transformation demands what OT was never designed to allow: continuous data exchange between control systems and the outside world. To enable this, most organisations resorted to layering on complexity — adding firewalls, demilitarised zones (DMZs), and data brokers to bridge the gap between IT and OT networks. While these architectures create a path for integration, they also expand the attack surface, introducing new points of failure and constant maintenance overhead. The result is a fragile compromise: partial connectivity that neither delivers full insight nor ensures complete security.

Firewalls and DMZs were meant to be safeguards, but in practice, they’ve become bandages over a deeper architectural flaw. Each added layer assumes that perimeters can be perfectly defined — that threats stay outside while trusted systems stay inside. In reality, modern industrial networks blur these boundaries. Data flows continuously between vendors, cloud services, and remote operators, erasing the notion of a fixed “inside.” Attackers no longer need to breach a single wall; they exploit misconfigurations, outdated firmware, or even legitimate remote connections. The result is a fragile illusion of safety — one that gives comfort to compliance checklists but little protection against modern threats.
Common security pitfalls in today’s OT-IT integrations include:
For decades, cybersecurity progress has centred around IT — networks that are flexible, replaceable, and built on modern standards. But OT has always lived in another world. Control systems run on proprietary stacks, decades-old firmware, and hardware designed to last thirty years, not three. Concepts like zero trust, endpoint protection, or rapid patching simply don’t fit into environments where uptime trumps everything else. As a result, applying IT security models to OT networks has proven ineffective — a mismatch born from different priorities and timelines. The truth is, OT has never received the same level of innovation or attention from the broader cybersecurity community, and today’s industrial security gap is the consequence of that neglect.
For many industrial operators, the security gap isn’t a matter of negligence — it’s structural. They depend on vendor ecosystems that were never built for the cloud era. Most SCADA systems still run on Windows servers with outdated authentication like LDAP or domain credentials, because that’s how the vendors designed them. Integrating AI or analytics means exposing these systems to networks they were never meant to face. Even with the best intentions, users are left maintaining fragile bridges — patching, isolating, and hoping that compliance equals safety. The truth is, the problem isn’t poor practice; it’s that the technology itself was never ready for the connected world.
The challenges facing OT aren’t small — they’re systemic. Firewalls, DMZs, and patchwork integrations can’t solve a problem rooted in decades of architectural separation. What’s needed isn’t another security layer, but a new foundation — one that reconnects reliability with adaptability.
VeilNet Private Plane was built precisely for this transformation. It creates an absolutely isolated network on top of a physically connected one — a secure “air gap within the internet.” Within this plane, vendors’ cloud platforms, on-prem systems, and intelligent devices coexist as if they were on the same local network, without ever exposing a single open port. Instead of sending data outward to vendor clouds, VeilNet brings those services inward — into your controlled environment — where you manage them as your own.
This approach bridges the past and the future: preserving the safety of OT isolation while enabling the intelligence and agility of AI-driven operations.
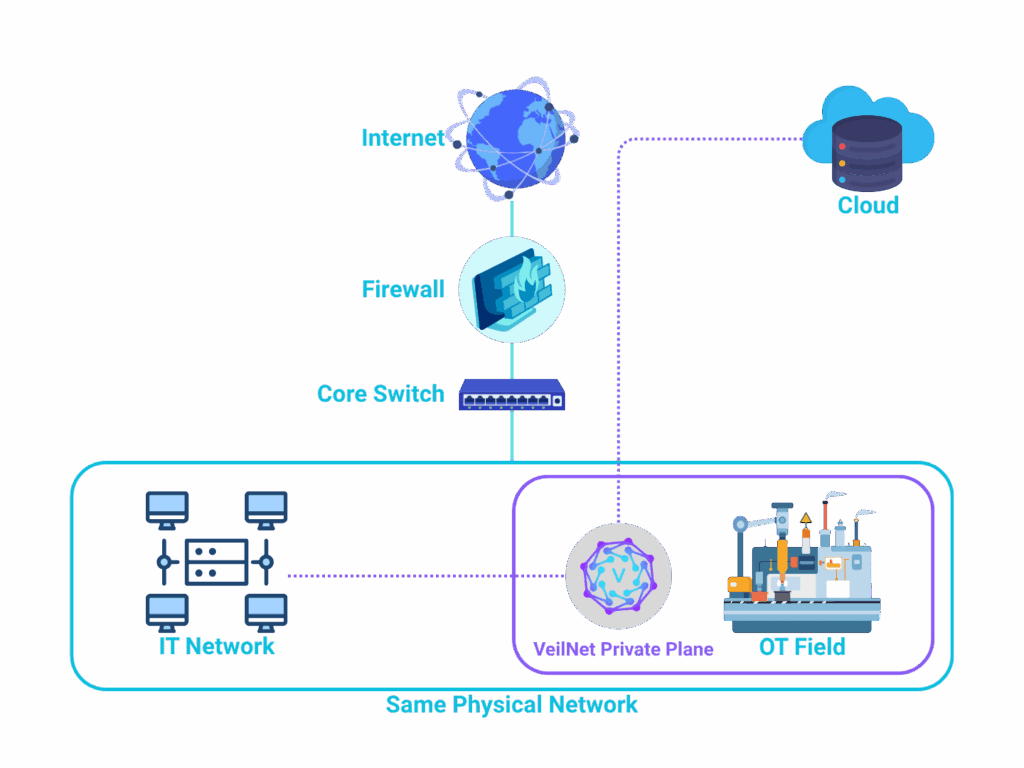
At its core, VeilNet Private Plane uses post-quantum cryptography and an AI-routed overlay network to form an invisible communication layer above existing infrastructure. Every connection is ephemeral — established only when needed and bound to the network gateways instead of the hosts. This design makes interception or imitation technically impossible. Unlike traditional VPNs or SD-WANs, VeilNet does not expose static IPs, open ports, or coordination servers. Each Plane behaves as a self-contained environment, where only authorised devices and vendor clouds can communicate through cryptographically verified sessions.
VeilNet’s topology is self-healing and adaptive: it avoids mesh sprawl, balances load intelligently, and scales across data centres, edge devices, and AI clusters without manual configuration. The result is a network that’s both invisible and intelligent — delivering true isolation without the need to disconnect.
Traditional air gaps and DMZs were built on the assumption that physical separation equals safety. But once that barrier is breached — whether through a misconfigured port, a USB drive, or a compromised remote link — there’s nothing left to protect the core systems. Physical isolation is static; it cannot adapt or detect intrusion once connectivity is established.
VeilNet Private Plane goes far beyond this outdated model. It provides dynamic, cryptographically enforced isolation — even across a unified physical network. Every packet is authenticated and encrypted using post-quantum algorithms (Kyber KEM and Dilithium DSA), making traditional OT protocol weaknesses irrelevant. Even if an attacker gains access to the underlying network, the traffic within the Plane is indistinguishable, untraceable, and unlinkable to specific systems or services.
Why VeilNet Private Plane surpasses traditional air gaps and DMZs:
VeilNet doesn’t just replicate the safety of an air gap — it evolves it into something smarter, adaptive, and future-proof.
Most VPNs were never designed for the industrial world. They were built for small networks of laptops, not thousands of controllers, gateways, and sensors constantly exchanging real-time data. To achieve connectivity, these systems rely on mesh topologies — where every node must maintain a direct relationship with every other node. It works for a handful of devices, but quickly collapses under industrial scale.
In a mesh VPN:
This is why overlay VPNs like Tailscale, ZeroTier, or Nebula are ideal for remote access, but unsuitable for continuous OT workloads. Industrial environments don’t need millions of connections — they need intelligent, context-aware connectivity that scales effortlessly.
VeilNet Private Plane replaces the exponential complexity of mesh networking with an AI-routed, ephemeral topology. Devices connect through dynamic paths that form and dissolve as needed, maintaining end-to-end encryption and quantum-safe security without the combinatorial explosion of links. It scales from a single PLC to an entire global operation — seamlessly, securely, and autonomously.
With VeilNet, the era of simply “connecting machines” gives way to something far greater — factories that operate as clouds. Each plant, sensor, and controller becomes part of a globally unified, post-quantum secure network that scales without limits. Instead of isolated facilities exchanging data through fragile middleware, VeilNet links every site, region, and vendor under one intelligent interconnect — where AI can analyse, coordinate, and optimize production in real time. It’s not Industry 4.0 anymore; it’s the foundation for the next industrial age, where adaptability, intelligence, and security coexist by design.
The business impact is immediate:
VeilNet doesn’t just connect factories to the cloud — it turns the factory into the cloud: secure, intelligent, and infinitely scalable.